Rocky the Raptor here, RPost’s cybersecurity product evangelist. Here’s the thing about 2026: your “digital transactions” aren’t just transactions anymore; they’re content-rich moments where money, intent, identity, and urgency all collide.
Hi, Armand here, RPost’s intelligent content product evangelist armadillo. The first week of 2026 is almost already in the books (yeah, time is doing that thing again), and I’ve been thinking back to last year’s Gartner conferences.
Rocky the Raptor here, RPost’s cybersecurity product evangelist, with some early 2026 insights.
A back-and-forth conversation between Rocky the Raptor (Cybersecurity Evangelist) and Armand the Armadillo (Workflow Automation Evangelist) at RPost
Rocky the raptor here, RPost’s cybersecurity product evangelist. I was in the ski shop the other day, doing what every raptor does around the holidays: soaking in the gear aisle and pretending I need new equipment 😊 I spotted a shiny new ski boot buckle gadget. Sleek. Clever. Possibly unnecessary.

January 16, 2026
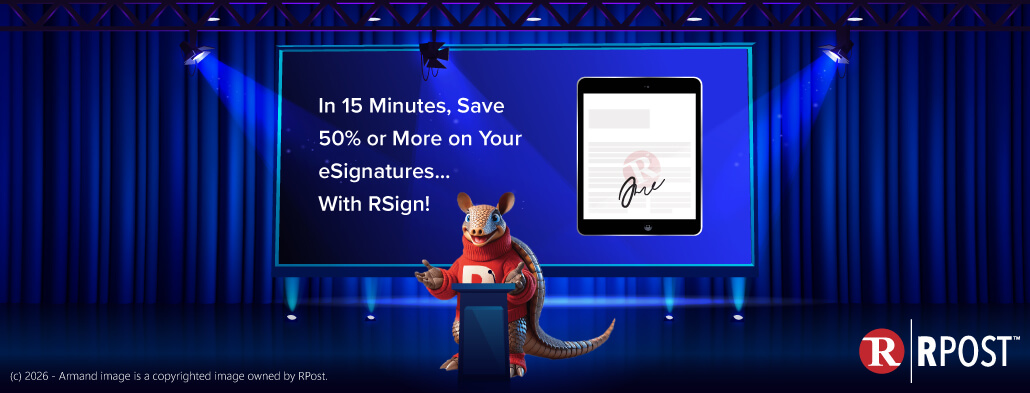
January 09, 2026

January 05, 2026

December 26, 2025
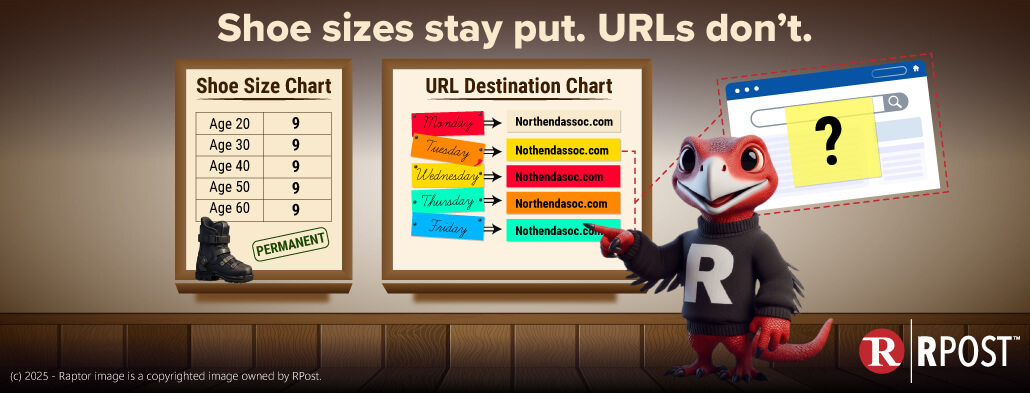
December 19, 2025